
Legal
HB 3749, Greg Abbott, and... John Oliver?
HBO's Last Week Tonight with John Oliver discussed public concerns about how med spas operate.By Alex Thiersch, CEO, AmSpaJohn Oliver ...
Posted By Mike Meyer, Monday, February 15, 2021

By Kerri Flores, Heffernan Insurance Brokers
The health care industry is under attack. In late October 2020, the Cybersecurity & Infrastructure Security Agency (CISA), along with the Federal Bureau of Investigation (FBI) and the Department of Health and Human Services (HHS), issued an advisory warning that cybercriminals were launching a ransomware attack against the health care industry. This is merely the latest in a long string of cyber threats against the industry. Following are the three most common and harmful cyber threats for your business to be aware of in 2021 and beyond.
Modern health care facilities depend on electronic health records and other digital tools. If a ransomware program infects a facility's computer system and encrypts the files, regular operations may become impossible until the files are recovered. This actually happened in 2017 when the WannaCry ransomware attack forced some hospitals in the United Kingdom to cancel appointments and divert patients.
Ransomware attacks can cause expensive disruptions for all kinds of organizations, but for health care facilities, they can prove downright deadly. According to the National Law Review, various news reports indicate that a patient in Germany died after a ransomware attack delayed the urgent medical treatment she needed. This is believed to be the first death directly linked to a cyberattack on a hospital, but it may not be the last.
The FBI has urged organizations not to pay ransomware demands, as doing so can fund criminal activity and encourage more attacks, while there is no guarantee that files will be restored as promised. The U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) also has issued an advisory warning that ransomware payments could violate OFAC regulations. Nevertheless, faced with no other way to resume operations, many organizations have decided they have no choice but to pay up.
The situation can become even more desperate with new versions of ransomware that don't simply encrypt data to make it unusable, but also threaten to release the data to the public.
Now, CISA, the FBI and HHS are warning about a cyberattack targeting health care organizations. According to the advisory issued in late October, malicious cyber actors are using TrickBot and BazarLoader malware to target the health care and public health sectors. The malware can result in ransomware, data theft and disruption. The advisory also warns that dealing with this threat during the coronavirus pandemic may become especially difficult.
TrickBot malware can be used to infect computer systems with Ryuk ransomware. Once Ryuk infects a system, the attackers typically demand payment via Bitcoin to have the files restored. Ryuk can also interfere with security applications that may be in place to prevent malware. This is an especially dangerous type of ransomware that has been associated with numerous, often very targeted attacks that result in large ransom demands.
Health care facilities are especially vulnerable to cyberattacks because they have highly valuable patient records. Without access to this data, operations can be severely disrupted, and this can quickly become a matter of life and death for the patients impacted by the disruption. This means that hospitals may be willing to pay up quickly to restore operations as soon as possible.
All this data also makes health care facilities vulnerable to another threat: data breaches. Personal data is often sold on the black market. Medical records, which can be used in identity theft, fetch an especially high price.
Data breaches can occur in multiple ways. In some cases, they are linked to malware attacks, and some new ransomware attacks have included threats to expose data. Data breaches can also stem from computer vulnerabilities that allow hackers to access data.
Not all data breaches have high-tech roots, though. Data breaches can also occur when flash drives, laptops, other pieces of electronic equipment or even paper documents containing sensitive data are lost or stolen and fall into the wrong hands. It's also possible for employees or former employees to provide access accidentally or maliciously, or because they'e been tricked by someone.
Regardless of the cause, a data breach is a serious issue. Organizations that experience data breaches must follow data breach notification laws, and this can be costly. At the same time, organizations may be hit with regulatory fines for failing to keep records safe.
Fines are especially likely for health care organizations that must comply with HIPAA regulations. The HHS newsroom has numerous reports of organizations that were fined following potential data breaches, including these recent examples:
Cyber threats often rely on human error. Cybercriminals may use schemes to try to trick people into clicking malicious links, opening malicious attachments or providing sensitive information that can be used to launch an attack. Phishing attacks—and the similar but more targeted spear phishing attacks— often appear as legitimate correspondences, but are, in fact, launched by malicious cyber actors.
Business email compromise (BEC) schemes have emerged as especially insidious threats. In these schemes, the perpetrator typically targets a victim by posing as a legitimate party—such as a CEO, vendor or client—and engages in email communications to gain the victim's trust. Then the perpetrator will request a wire transfer or other transaction. In 2019, the FBI's Internet Crime Complaint Center received 23,775 complaints about BEC schemes and documented more than $1.7 billion in losses.
Health care organizations, like other types of organizations, are vulnerable to these attacks. Malicious cyber actors may also pose as health care organizations, the World Health Organization or the U.S. Centers for Disease Control and Prevention to manipulate individuals.
To cybercriminals looking for valuable data, health care organizations might as well have targets on their backs. To avoid potentially devastating disruption and costs, proactive cybersecurity measures are needed.
Finally, be sure to protect your organization with robust cyber insurance. (See sidebar.) In today's world, cyber coverage is not a nice-to-have—it's a must-have. When you purchase coverage, your insurer may provide some valuable extras—such as risk assessment, compliance review and training—to help you prevent losses. If you're the victim of a cyberattack, your coverage will provide guidance and resources to help you control the damage.
AmSpa members receive QP every quarter. Click here to learn how to become a member and make your med spa the next aesthetic success story.
Kerri Flores is a client advocate at Heffernan Insurance Brokers. She specializes in helping health care businesses with their short- and long-term insurance goals. With five years of experience in the industry, she has helped hundreds of clients by finding innovative, reliable and cost-efficient methods of transferring risk. She can be contacted at 925.448.2612 or kerrif@heffins.com.
Related Tags
Medical spa news, blogs and updates sent directly to your inbox.

Legal
HBO's Last Week Tonight with John Oliver discussed public concerns about how med spas operate.By Alex Thiersch, CEO, AmSpaJohn Oliver ...

Trends
By Patrick O'Brien, JD, general counsel, and Kirstie Jackson, director of education, American Med Spa AssociationWhat is happening with glucagon-like ...
Trends
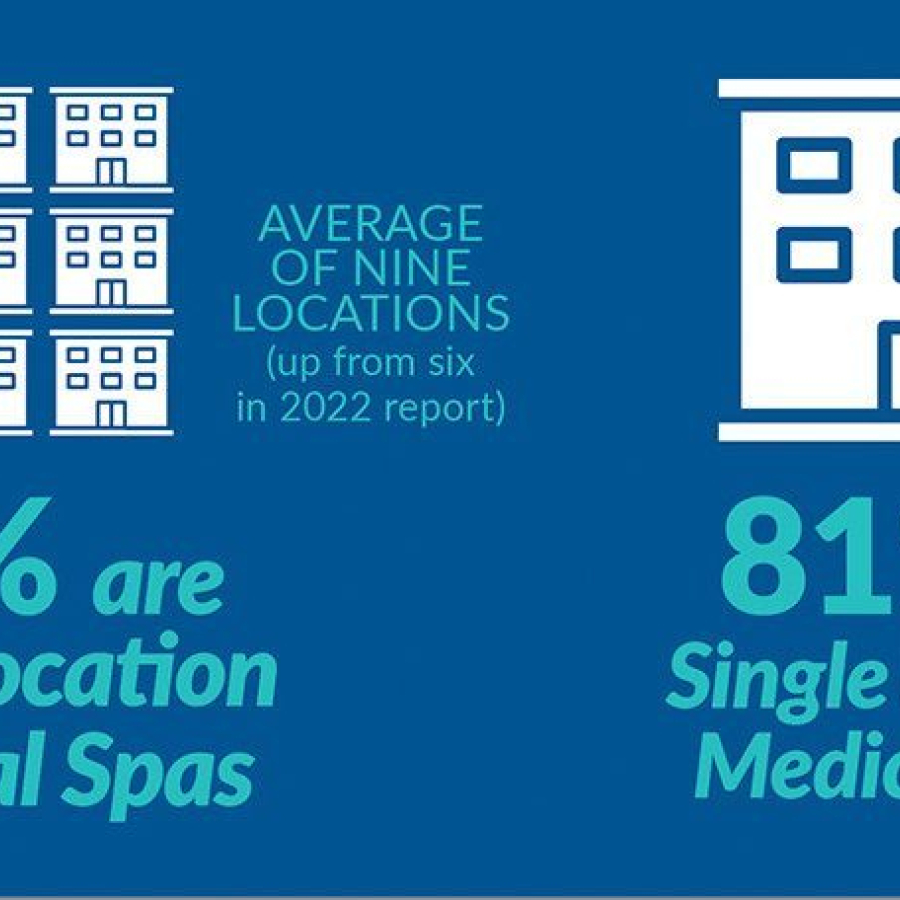
By Michael Meyer Approximately every two years, the American Med Spa Association (AmSpa) releases its Medical Spa State of ...

Trends
By Michael Meyer Since the beginning of 2024, it seems like medical aesthetics has taken one hit after another ...